mirror of
https://github.com/AFLplusplus/AFLplusplus.git
synced 2025-06-11 17:51:32 +00:00
updated unicornafl
This commit is contained in:
2
.gitignore
vendored
2
.gitignore
vendored
@ -18,6 +18,7 @@ afl-gcc-fast
|
||||
afl-g++-fast
|
||||
afl-gotcpu
|
||||
afl-ld
|
||||
afl-ld-lto
|
||||
afl-qemu-trace
|
||||
afl-showmap
|
||||
afl-tmin
|
||||
@ -45,6 +46,7 @@ ld
|
||||
qemu_mode/qemu-*
|
||||
unicorn_mode/samples/*/\.test-*
|
||||
unicorn_mode/samples/*/output/
|
||||
unicorn_mode/unicornafl
|
||||
core\.*
|
||||
test/unittests/unit_maybe_alloc
|
||||
test/unittests/unit_preallocable
|
||||
|
||||
24
GNUmakefile
24
GNUmakefile
@ -121,7 +121,7 @@ endif
|
||||
|
||||
ifeq "$(shell uname -s)" "Haiku"
|
||||
SHMAT_OK=0
|
||||
override CFLAGS += -DUSEMMAP=1 -Wno-error=format -fpic
|
||||
override CFLAGS += -DUSEMMAP=1 -Wno-error=format -fPIC
|
||||
LDFLAGS+=-Wno-deprecated-declarations -lgnu
|
||||
SPECIAL_PERFORMANCE += -DUSEMMAP=1
|
||||
endif
|
||||
@ -282,8 +282,8 @@ help:
|
||||
@echo "HELP --- the following make targets exist:"
|
||||
@echo "=========================================="
|
||||
@echo "all: just the main afl++ binaries"
|
||||
@echo "binary-only: everything for binary-only fuzzing: qemu_mode, unicorn_mode, libdislocator, libtokencap, radamsa"
|
||||
@echo "source-only: everything for source code fuzzing: llvm_mode, gcc_plugin, libdislocator, libtokencap, radamsa"
|
||||
@echo "binary-only: everything for binary-only fuzzing: qemu_mode, unicorn_mode, libdislocator, libtokencap"
|
||||
@echo "source-only: everything for source code fuzzing: llvm_mode, gcc_plugin, libdislocator, libtokencap"
|
||||
@echo "distrib: everything (for both binary-only and source code fuzzing)"
|
||||
@echo "man: creates simple man pages from the help option of the programs"
|
||||
@echo "install: installs everything you have compiled with the build option above"
|
||||
@ -311,6 +311,8 @@ ifndef AFL_NO_X86
|
||||
test_x86:
|
||||
@echo "[*] Checking for the default compiler cc..."
|
||||
@type $(CC) >/dev/null || ( echo; echo "Oops, looks like there is no compiler '"$(CC)"' in your path."; echo; echo "Don't panic! You can restart with '"$(_)" CC=<yourCcompiler>'."; echo; exit 1 )
|
||||
@echo "[*] Testing the PATH environment variable..."
|
||||
@test "$${PATH}" != "$${PATH#.:}" && { echo "Please remove current directory '.' from PATH to avoid recursion of 'as', thanks!"; echo; exit 1; } || :
|
||||
@echo "[*] Checking for the ability to compile x86 code..."
|
||||
@echo 'main() { __asm__("xorb %al, %al"); }' | $(CC) $(CFLAGS) -w -x c - -o .test1 || ( echo; echo "Oops, looks like your compiler can't generate x86 code."; echo; echo "Don't panic! You can use the LLVM or QEMU mode, but see docs/INSTALL first."; echo "(To ignore this error, set AFL_NO_X86=1 and try again.)"; echo; exit 1 )
|
||||
@rm -f .test1
|
||||
@ -374,12 +376,6 @@ src/afl-forkserver.o : $(COMM_HDR) src/afl-forkserver.c include/forkserver.h
|
||||
src/afl-sharedmem.o : $(COMM_HDR) src/afl-sharedmem.c include/sharedmem.h
|
||||
$(CC) $(CFLAGS) $(CFLAGS_FLTO) -c src/afl-sharedmem.c -o src/afl-sharedmem.o
|
||||
|
||||
radamsa: src/third_party/libradamsa/libradamsa.so
|
||||
cp src/third_party/libradamsa/libradamsa.so .
|
||||
|
||||
src/third_party/libradamsa/libradamsa.so: src/third_party/libradamsa/libradamsa.c src/third_party/libradamsa/radamsa.h
|
||||
$(MAKE) -C src/third_party/libradamsa/ CFLAGS="$(CFLAGS)"
|
||||
|
||||
afl-fuzz: $(COMM_HDR) include/afl-fuzz.h $(AFL_FUZZ_FILES) src/afl-common.o src/afl-sharedmem.o src/afl-forkserver.o src/afl-performance.o | test_x86
|
||||
$(CC) $(CFLAGS) $(COMPILE_STATIC) $(CFLAGS_FLTO) $(AFL_FUZZ_FILES) src/afl-common.o src/afl-sharedmem.o src/afl-forkserver.o src/afl-performance.o -o $@ $(PYFLAGS) $(LDFLAGS)
|
||||
|
||||
@ -460,6 +456,8 @@ code-format:
|
||||
./.custom-format.py -i gcc_plugin/*.c
|
||||
#./.custom-format.py -i gcc_plugin/*.h
|
||||
./.custom-format.py -i gcc_plugin/*.cc
|
||||
./.custom-format.py -i custom_mutators/*/*.c
|
||||
./.custom-format.py -i custom_mutators/*/*.h
|
||||
./.custom-format.py -i examples/*/*.c
|
||||
./.custom-format.py -i examples/*/*.h
|
||||
./.custom-format.py -i test/*.c
|
||||
@ -512,7 +510,6 @@ clean:
|
||||
$(MAKE) -C examples/argv_fuzzing clean
|
||||
$(MAKE) -C qemu_mode/unsigaction clean
|
||||
$(MAKE) -C qemu_mode/libcompcov clean
|
||||
$(MAKE) -C src/third_party/libradamsa/ clean
|
||||
rm -rf qemu_mode/qemu-3.1.1
|
||||
ifeq "$(IN_REPO)" "1"
|
||||
test -d unicorn_mode/unicornafl && $(MAKE) -C unicorn_mode/unicornafl clean || true
|
||||
@ -526,7 +523,7 @@ deepclean: clean
|
||||
rm -rf unicorn_mode/unicornafl
|
||||
git reset --hard >/dev/null 2>&1 || true
|
||||
|
||||
distrib: all radamsa
|
||||
distrib: all
|
||||
-$(MAKE) -C llvm_mode
|
||||
-$(MAKE) -C gcc_plugin
|
||||
$(MAKE) -C libdislocator
|
||||
@ -537,7 +534,7 @@ distrib: all radamsa
|
||||
-cd qemu_mode && sh ./build_qemu_support.sh
|
||||
cd unicorn_mode && unset CFLAGS && sh ./build_unicorn_support.sh
|
||||
|
||||
binary-only: all radamsa
|
||||
binary-only: all
|
||||
$(MAKE) -C libdislocator
|
||||
$(MAKE) -C libtokencap
|
||||
$(MAKE) -C examples/afl_network_proxy
|
||||
@ -546,7 +543,7 @@ binary-only: all radamsa
|
||||
-cd qemu_mode && sh ./build_qemu_support.sh
|
||||
cd unicorn_mode && unset CFLAGS && sh ./build_unicorn_support.sh
|
||||
|
||||
source-only: all radamsa
|
||||
source-only: all
|
||||
-$(MAKE) -C llvm_mode
|
||||
-$(MAKE) -C gcc_plugin
|
||||
$(MAKE) -C libdislocator
|
||||
@ -585,7 +582,6 @@ install: all $(MANPAGES)
|
||||
if [ -f libdislocator.so ]; then set -e; install -m 755 libdislocator.so $${DESTDIR}$(HELPER_PATH); fi
|
||||
if [ -f libtokencap.so ]; then set -e; install -m 755 libtokencap.so $${DESTDIR}$(HELPER_PATH); fi
|
||||
if [ -f libcompcov.so ]; then set -e; install -m 755 libcompcov.so $${DESTDIR}$(HELPER_PATH); fi
|
||||
if [ -f libradamsa.so ]; then set -e; install -m 755 libradamsa.so $${DESTDIR}$(HELPER_PATH); fi
|
||||
if [ -f afl-fuzz-document ]; then set -e; install -m 755 afl-fuzz-document $${DESTDIR}$(BIN_PATH); fi
|
||||
if [ -f socketfuzz32.so -o -f socketfuzz64.so ]; then $(MAKE) -C examples/socket_fuzzing install; fi
|
||||
if [ -f argvfuzz32.so -o -f argvfuzz64.so ]; then $(MAKE) -C examples/argv_fuzzing install; fi
|
||||
|
||||
@ -54,7 +54,7 @@
|
||||
|
||||
* Win32 PE binary-only fuzzing with QEMU and Wine
|
||||
|
||||
* Radamsa mutator (enable with `-R` to add or `-RR` to run it exclusively).
|
||||
* Radamsa mutator (as a custom mutator).
|
||||
|
||||
* QBDI mode to fuzz android native libraries via QBDI framework
|
||||
|
||||
@ -167,8 +167,8 @@ is what you should choose.
|
||||
These build targets exist:
|
||||
|
||||
* all: just the main afl++ binaries
|
||||
* binary-only: everything for binary-only fuzzing: qemu_mode, unicorn_mode, libdislocator, libtokencap, radamsa
|
||||
* source-only: everything for source code fuzzing: llvm_mode, libdislocator, libtokencap, radamsa
|
||||
* binary-only: everything for binary-only fuzzing: qemu_mode, unicorn_mode, libdislocator, libtokencap
|
||||
* source-only: everything for source code fuzzing: llvm_mode, libdislocator, libtokencap
|
||||
* distrib: everything (for both binary-only and source code fuzzing)
|
||||
* man: creates simple man pages from the help option of the programs
|
||||
* install: installs everything you have compiled with the build options above
|
||||
|
||||
3
TODO.md
3
TODO.md
@ -15,6 +15,9 @@ afl-fuzz:
|
||||
- ascii_only mode for mutation output - or use a custom mutator for this?
|
||||
- setting min_len/max_len/start_offset/end_offset limits for mutation output
|
||||
|
||||
llvm_mode:
|
||||
- LTO - imitate sancov
|
||||
|
||||
gcc_plugin:
|
||||
- (wait for submission then decide)
|
||||
- laf-intel
|
||||
|
||||
12
custom_mutators/README.md
Normal file
12
custom_mutators/README.md
Normal file
@ -0,0 +1,12 @@
|
||||
# production ready custom mutators
|
||||
|
||||
This directory holds ready to use custom mutators.
|
||||
Just type "make" in the individual subdirectories.
|
||||
|
||||
Use with e.g.
|
||||
|
||||
`AFL_CUSTOM_MUTATOR_LIBRARY=custom_mutators/radamsa/radamsa-mutator.so afl-fuzz ....`
|
||||
|
||||
and add `AFL_CUSTOM_MUTATOR_ONLY=1` if you only want to use the custom mutator.
|
||||
|
||||
Multiple custom mutators can be used by seperating their paths with `:` in the environment variable.
|
||||
@ -1,15 +1,15 @@
|
||||
CUR_DIR := $(shell dirname $(realpath $(lastword $(MAKEFILE_LIST))))
|
||||
|
||||
all: libradamsa.so
|
||||
all: radamsa-mutator.so
|
||||
|
||||
# These can be overriden:
|
||||
CFLAGS ?= -march=native $(CFLAGS_FLTO)
|
||||
CFLAGS ?= $(CFLAGS_FLTO)
|
||||
|
||||
# These are required: (otherwise radamsa gets very very slooooow)
|
||||
CFLAGS += -O3 -funroll-loops
|
||||
|
||||
libradamsa.so: libradamsa.a
|
||||
$(CC) $(CFLAGS) -shared libradamsa.a -o libradamsa.so
|
||||
#libradamsa.so: libradamsa.a
|
||||
# $(CC) $(CFLAGS) -shared libradamsa.a -o libradamsa.so
|
||||
|
||||
libradamsa.a: libradamsa.c radamsa.h
|
||||
@echo " ***************************************************************"
|
||||
@ -17,10 +17,14 @@ libradamsa.a: libradamsa.c radamsa.h
|
||||
@echo " ***************************************************************"
|
||||
$(CC) -fPIC $(CFLAGS) -I $(CUR_DIR) -o libradamsa.a -c libradamsa.c
|
||||
|
||||
radamsa-mutator.so: radamsa-mutator.c libradamsa.a
|
||||
$(CC) $(CFLAGS) -g -I. -I../../include -shared -fPIC -c radamsa-mutator.c
|
||||
$(CC) $(CFLAGS) -shared -fPIC -o radamsa-mutator.so radamsa-mutator.o libradamsa.a
|
||||
|
||||
test: libradamsa.a libradamsa-test.c
|
||||
$(CC) $(CFLAGS) -I $(CUR_DIR) -o libradamsa-test libradamsa-test.c libradamsa.a
|
||||
./libradamsa-test libradamsa-test.c | grep "library test passed"
|
||||
rm /tmp/libradamsa-*.fuzz
|
||||
|
||||
clean:
|
||||
rm -f libradamsa.a libradamsa.so libradamsa-test
|
||||
rm -f radamsa-mutator.so libradamsa.a libradamsa-test *.o *~ core
|
||||
@ -1,4 +1,4 @@
|
||||
# libradamsa
|
||||
# custum mutator: libradamsa
|
||||
|
||||
Pretranslated radamsa library. This code belongs to the radamsa author.
|
||||
|
||||
342
custom_mutators/radamsa/custom_mutator_helpers.h
Normal file
342
custom_mutators/radamsa/custom_mutator_helpers.h
Normal file
@ -0,0 +1,342 @@
|
||||
#ifndef CUSTOM_MUTATOR_HELPERS
|
||||
#define CUSTOM_MUTATOR_HELPERS
|
||||
|
||||
#include "config.h"
|
||||
#include "types.h"
|
||||
#include <stdlib.h>
|
||||
|
||||
#define INITIAL_GROWTH_SIZE (64)
|
||||
|
||||
#define RAND_BELOW(limit) (rand() % (limit))
|
||||
|
||||
/* Use in a struct: creates a name_buf and a name_size variable. */
|
||||
#define BUF_VAR(type, name) \
|
||||
type * name##_buf; \
|
||||
size_t name##_size;
|
||||
/* this filles in `&structptr->something_buf, &structptr->something_size`. */
|
||||
#define BUF_PARAMS(struct, name) \
|
||||
(void **)&struct->name##_buf, &struct->name##_size
|
||||
|
||||
typedef struct {
|
||||
|
||||
} afl_t;
|
||||
|
||||
static void surgical_havoc_mutate(u8 *out_buf, s32 begin, s32 end) {
|
||||
|
||||
static s8 interesting_8[] = {INTERESTING_8};
|
||||
static s16 interesting_16[] = {INTERESTING_8, INTERESTING_16};
|
||||
static s32 interesting_32[] = {INTERESTING_8, INTERESTING_16, INTERESTING_32};
|
||||
|
||||
switch (RAND_BELOW(12)) {
|
||||
|
||||
case 0: {
|
||||
|
||||
/* Flip a single bit somewhere. Spooky! */
|
||||
|
||||
s32 bit_idx = ((RAND_BELOW(end - begin) + begin) << 3) + RAND_BELOW(8);
|
||||
|
||||
out_buf[bit_idx >> 3] ^= 128 >> (bit_idx & 7);
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 1: {
|
||||
|
||||
/* Set byte to interesting value. */
|
||||
|
||||
u8 val = interesting_8[RAND_BELOW(sizeof(interesting_8))];
|
||||
out_buf[(RAND_BELOW(end - begin) + begin)] = val;
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 2: {
|
||||
|
||||
/* Set word to interesting value, randomly choosing endian. */
|
||||
|
||||
if (end - begin < 2) break;
|
||||
|
||||
s32 byte_idx = (RAND_BELOW(end - begin) + begin);
|
||||
|
||||
if (byte_idx >= end - 1) break;
|
||||
|
||||
switch (RAND_BELOW(2)) {
|
||||
|
||||
case 0:
|
||||
*(u16 *)(out_buf + byte_idx) =
|
||||
interesting_16[RAND_BELOW(sizeof(interesting_16) >> 1)];
|
||||
break;
|
||||
case 1:
|
||||
*(u16 *)(out_buf + byte_idx) =
|
||||
SWAP16(interesting_16[RAND_BELOW(sizeof(interesting_16) >> 1)]);
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 3: {
|
||||
|
||||
/* Set dword to interesting value, randomly choosing endian. */
|
||||
|
||||
if (end - begin < 4) break;
|
||||
|
||||
s32 byte_idx = (RAND_BELOW(end - begin) + begin);
|
||||
|
||||
if (byte_idx >= end - 3) break;
|
||||
|
||||
switch (RAND_BELOW(2)) {
|
||||
|
||||
case 0:
|
||||
*(u32 *)(out_buf + byte_idx) =
|
||||
interesting_32[RAND_BELOW(sizeof(interesting_32) >> 2)];
|
||||
break;
|
||||
case 1:
|
||||
*(u32 *)(out_buf + byte_idx) =
|
||||
SWAP32(interesting_32[RAND_BELOW(sizeof(interesting_32) >> 2)]);
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 4: {
|
||||
|
||||
/* Set qword to interesting value, randomly choosing endian. */
|
||||
|
||||
if (end - begin < 8) break;
|
||||
|
||||
s32 byte_idx = (RAND_BELOW(end - begin) + begin);
|
||||
|
||||
if (byte_idx >= end - 7) break;
|
||||
|
||||
switch (RAND_BELOW(2)) {
|
||||
|
||||
case 0:
|
||||
*(u64 *)(out_buf + byte_idx) =
|
||||
(s64)interesting_32[RAND_BELOW(sizeof(interesting_32) >> 2)];
|
||||
break;
|
||||
case 1:
|
||||
*(u64 *)(out_buf + byte_idx) = SWAP64(
|
||||
(s64)interesting_32[RAND_BELOW(sizeof(interesting_32) >> 2)]);
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 5: {
|
||||
|
||||
/* Randomly subtract from byte. */
|
||||
|
||||
out_buf[(RAND_BELOW(end - begin) + begin)] -= 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 6: {
|
||||
|
||||
/* Randomly add to byte. */
|
||||
|
||||
out_buf[(RAND_BELOW(end - begin) + begin)] += 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 7: {
|
||||
|
||||
/* Randomly subtract from word, random endian. */
|
||||
|
||||
if (end - begin < 2) break;
|
||||
|
||||
s32 byte_idx = (RAND_BELOW(end - begin) + begin);
|
||||
|
||||
if (byte_idx >= end - 1) break;
|
||||
|
||||
if (RAND_BELOW(2)) {
|
||||
|
||||
*(u16 *)(out_buf + byte_idx) -= 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
} else {
|
||||
|
||||
u16 num = 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
*(u16 *)(out_buf + byte_idx) =
|
||||
SWAP16(SWAP16(*(u16 *)(out_buf + byte_idx)) - num);
|
||||
|
||||
}
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 8: {
|
||||
|
||||
/* Randomly add to word, random endian. */
|
||||
|
||||
if (end - begin < 2) break;
|
||||
|
||||
s32 byte_idx = (RAND_BELOW(end - begin) + begin);
|
||||
|
||||
if (byte_idx >= end - 1) break;
|
||||
|
||||
if (RAND_BELOW(2)) {
|
||||
|
||||
*(u16 *)(out_buf + byte_idx) += 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
} else {
|
||||
|
||||
u16 num = 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
*(u16 *)(out_buf + byte_idx) =
|
||||
SWAP16(SWAP16(*(u16 *)(out_buf + byte_idx)) + num);
|
||||
|
||||
}
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 9: {
|
||||
|
||||
/* Randomly subtract from dword, random endian. */
|
||||
|
||||
if (end - begin < 4) break;
|
||||
|
||||
s32 byte_idx = (RAND_BELOW(end - begin) + begin);
|
||||
|
||||
if (byte_idx >= end - 3) break;
|
||||
|
||||
if (RAND_BELOW(2)) {
|
||||
|
||||
*(u32 *)(out_buf + byte_idx) -= 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
} else {
|
||||
|
||||
u32 num = 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
*(u32 *)(out_buf + byte_idx) =
|
||||
SWAP32(SWAP32(*(u32 *)(out_buf + byte_idx)) - num);
|
||||
|
||||
}
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 10: {
|
||||
|
||||
/* Randomly add to dword, random endian. */
|
||||
|
||||
if (end - begin < 4) break;
|
||||
|
||||
s32 byte_idx = (RAND_BELOW(end - begin) + begin);
|
||||
|
||||
if (byte_idx >= end - 3) break;
|
||||
|
||||
if (RAND_BELOW(2)) {
|
||||
|
||||
*(u32 *)(out_buf + byte_idx) += 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
} else {
|
||||
|
||||
u32 num = 1 + RAND_BELOW(ARITH_MAX);
|
||||
|
||||
*(u32 *)(out_buf + byte_idx) =
|
||||
SWAP32(SWAP32(*(u32 *)(out_buf + byte_idx)) + num);
|
||||
|
||||
}
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
case 11: {
|
||||
|
||||
/* Just set a random byte to a random value. Because,
|
||||
why not. We use XOR with 1-255 to eliminate the
|
||||
possibility of a no-op. */
|
||||
|
||||
out_buf[(RAND_BELOW(end - begin) + begin)] ^= 1 + RAND_BELOW(255);
|
||||
|
||||
break;
|
||||
|
||||
}
|
||||
|
||||
}
|
||||
|
||||
}
|
||||
|
||||
/* This function calculates the next power of 2 greater or equal its argument.
|
||||
@return The rounded up power of 2 (if no overflow) or 0 on overflow.
|
||||
*/
|
||||
static inline size_t next_pow2(size_t in) {
|
||||
|
||||
if (in == 0 || in > (size_t)-1)
|
||||
return 0; /* avoid undefined behaviour under-/overflow */
|
||||
size_t out = in - 1;
|
||||
out |= out >> 1;
|
||||
out |= out >> 2;
|
||||
out |= out >> 4;
|
||||
out |= out >> 8;
|
||||
out |= out >> 16;
|
||||
return out + 1;
|
||||
|
||||
}
|
||||
|
||||
/* This function makes sure *size is > size_needed after call.
|
||||
It will realloc *buf otherwise.
|
||||
*size will grow exponentially as per:
|
||||
https://blog.mozilla.org/nnethercote/2014/11/04/please-grow-your-buffers-exponentially/
|
||||
Will return NULL and free *buf if size_needed is <1 or realloc failed.
|
||||
@return For convenience, this function returns *buf.
|
||||
*/
|
||||
static inline void *maybe_grow(void **buf, size_t *size, size_t size_needed) {
|
||||
|
||||
/* No need to realloc */
|
||||
if (likely(size_needed && *size >= size_needed)) return *buf;
|
||||
|
||||
/* No initial size was set */
|
||||
if (size_needed < INITIAL_GROWTH_SIZE) size_needed = INITIAL_GROWTH_SIZE;
|
||||
|
||||
/* grow exponentially */
|
||||
size_t next_size = next_pow2(size_needed);
|
||||
|
||||
/* handle overflow */
|
||||
if (!next_size) { next_size = size_needed; }
|
||||
|
||||
/* alloc */
|
||||
*buf = realloc(*buf, next_size);
|
||||
*size = *buf ? next_size : 0;
|
||||
|
||||
return *buf;
|
||||
|
||||
}
|
||||
|
||||
/* Swaps buf1 ptr and buf2 ptr, as well as their sizes */
|
||||
static inline void swap_bufs(void **buf1, size_t *size1, void **buf2,
|
||||
size_t *size2) {
|
||||
|
||||
void * scratch_buf = *buf1;
|
||||
size_t scratch_size = *size1;
|
||||
*buf1 = *buf2;
|
||||
*size1 = *size2;
|
||||
*buf2 = scratch_buf;
|
||||
*size2 = scratch_size;
|
||||
|
||||
}
|
||||
|
||||
#undef INITIAL_GROWTH_SIZE
|
||||
|
||||
#endif
|
||||
|
||||
81
custom_mutators/radamsa/libradamsa-test.c
Normal file
81
custom_mutators/radamsa/libradamsa-test.c
Normal file
@ -0,0 +1,81 @@
|
||||
#include <radamsa.h>
|
||||
#include <stdio.h>
|
||||
#include <inttypes.h>
|
||||
#include <string.h>
|
||||
#include <stdlib.h>
|
||||
#include <sys/mman.h>
|
||||
#include <sys/types.h>
|
||||
#include <fcntl.h>
|
||||
#include <unistd.h>
|
||||
#include <sys/stat.h>
|
||||
|
||||
size_t filesize(char *filename) {
|
||||
|
||||
struct stat st;
|
||||
stat(filename, &st);
|
||||
return st.st_size;
|
||||
|
||||
}
|
||||
|
||||
#define BUFSIZE 1024 * 1024
|
||||
|
||||
void fail(char *why) {
|
||||
|
||||
printf("fail: %s\n", why);
|
||||
exit(1);
|
||||
|
||||
}
|
||||
|
||||
void write_output(char *data, size_t len, int num) {
|
||||
|
||||
char path[32];
|
||||
int fd;
|
||||
int wrote;
|
||||
sprintf(path, "/tmp/libradamsa-%d.fuzz", num);
|
||||
fd = open(path, O_WRONLY | O_CREAT | O_TRUNC, S_IRUSR | S_IWUSR);
|
||||
printf("Opened %s -> %d\n", path, fd);
|
||||
if (fd < 0) { fail("failed to open output file"); }
|
||||
wrote = write(fd, data, len);
|
||||
printf("wrote %d of %zu bytes\n", wrote, len);
|
||||
if (wrote != len) { fail("failed to write all of output at once"); }
|
||||
close(fd);
|
||||
printf("Wrote %zu bytes to %s\n", len, path);
|
||||
|
||||
}
|
||||
|
||||
int main(int nargs, char **argv) {
|
||||
|
||||
char * spath = argv[1];
|
||||
int fd = open(spath, O_RDONLY, 0);
|
||||
size_t len;
|
||||
char * input;
|
||||
char * output;
|
||||
int seed = 0;
|
||||
if (fd < 0) { fail("cannot open input file"); }
|
||||
len = filesize(spath);
|
||||
input = malloc(len);
|
||||
output = malloc(BUFSIZE);
|
||||
if (!input || !output) { fail("failed to allocate buffers\n"); }
|
||||
radamsa_init();
|
||||
if (len != read(fd, input, len)) {
|
||||
|
||||
fail("failed to read the entire sample at once");
|
||||
|
||||
}
|
||||
|
||||
while (seed++ < 100) {
|
||||
|
||||
size_t n;
|
||||
n = radamsa((uint8_t *)input, len, (uint8_t *)output, BUFSIZE, seed);
|
||||
write_output(output, n, seed);
|
||||
printf("Fuzzed %zu -> %zu bytes\n", len, n);
|
||||
|
||||
}
|
||||
|
||||
printf("library test passed\n");
|
||||
free(output);
|
||||
free(input);
|
||||
return 0;
|
||||
|
||||
}
|
||||
|
||||
61880
custom_mutators/radamsa/libradamsa.c
Normal file
61880
custom_mutators/radamsa/libradamsa.c
Normal file
File diff suppressed because it is too large
Load Diff
70
custom_mutators/radamsa/radamsa-mutator.c
Normal file
70
custom_mutators/radamsa/radamsa-mutator.c
Normal file
@ -0,0 +1,70 @@
|
||||
// This simple example just creates random buffer <= 100 filled with 'A'
|
||||
// needs -I /path/to/AFLplusplus/include
|
||||
//#include "custom_mutator_helpers.h"
|
||||
|
||||
#include <stdint.h>
|
||||
#include <stdlib.h>
|
||||
#include <string.h>
|
||||
#include <stdio.h>
|
||||
|
||||
#include "radamsa.h"
|
||||
#include "custom_mutator_helpers.h"
|
||||
|
||||
typedef struct my_mutator {
|
||||
|
||||
afl_t *afl;
|
||||
|
||||
u8 *mutator_buf;
|
||||
|
||||
unsigned int seed;
|
||||
|
||||
} my_mutator_t;
|
||||
|
||||
my_mutator_t *afl_custom_init(afl_t *afl, unsigned int seed) {
|
||||
|
||||
srand(seed);
|
||||
my_mutator_t *data = calloc(1, sizeof(my_mutator_t));
|
||||
if (!data) {
|
||||
|
||||
perror("afl_custom_init alloc");
|
||||
return NULL;
|
||||
|
||||
}
|
||||
|
||||
if ((data->mutator_buf = malloc(MAX_FILE)) == NULL) {
|
||||
|
||||
perror("mutator_buf alloc");
|
||||
return NULL;
|
||||
|
||||
}
|
||||
|
||||
data->afl = afl;
|
||||
data->seed = seed;
|
||||
|
||||
radamsa_init();
|
||||
|
||||
return data;
|
||||
|
||||
}
|
||||
|
||||
size_t afl_custom_fuzz(my_mutator_t *data, uint8_t *buf, size_t buf_size,
|
||||
u8 **out_buf, uint8_t *add_buf, size_t add_buf_size,
|
||||
size_t max_size) {
|
||||
|
||||
*out_buf = data->mutator_buf;
|
||||
return radamsa(buf, buf_size, data->mutator_buf, max_size, data->seed++);
|
||||
|
||||
}
|
||||
|
||||
/**
|
||||
* Deinitialize everything
|
||||
*
|
||||
* @param data The data ptr from afl_custom_init
|
||||
*/
|
||||
void afl_custom_deinit(my_mutator_t *data) {
|
||||
|
||||
free(data->mutator_buf);
|
||||
free(data);
|
||||
|
||||
}
|
||||
|
||||
10
custom_mutators/radamsa/radamsa.h
Normal file
10
custom_mutators/radamsa/radamsa.h
Normal file
@ -0,0 +1,10 @@
|
||||
#include <inttypes.h>
|
||||
#include <stddef.h>
|
||||
|
||||
void radamsa_init(void);
|
||||
|
||||
size_t radamsa(uint8_t *ptr, size_t len, uint8_t *target, size_t max,
|
||||
unsigned int seed);
|
||||
|
||||
size_t radamsa_inplace(uint8_t *ptr, size_t len, size_t max, unsigned int seed);
|
||||
|
||||
@ -14,6 +14,7 @@ sending a mail to <afl-users+subscribe@googlegroups.com>.
|
||||
- -S secondary nodes now only sync from the main node to increase
|
||||
performance, the -M main node still syncs from everyone. Added checks
|
||||
that ensure exactly one main node is present and warn otherwise
|
||||
- Add -D after -S to force a secondary to perform deterministic fuzzing
|
||||
- If no main node is present at a sync one secondary node automatically
|
||||
becomes a temporary main node until a real main nodes shows up
|
||||
- Fixed a mayor performance issue we inherited from AFLfast
|
||||
@ -23,6 +24,8 @@ sending a mail to <afl-users+subscribe@googlegroups.com>.
|
||||
- Ensure that the targets are killed on exit
|
||||
- fix/update to MOpt (thanks to arnow117)
|
||||
- added MOpt dictionary support from repo
|
||||
- added experimental SEEK power schedule. It is EXPLORE with ignoring
|
||||
the runtime and less focus on the length of the test case
|
||||
- llvm_mode:
|
||||
- the default instrumentation is now PCGUARD if the llvm version is >= 7,
|
||||
as it is faster and provides better coverage. The original afl
|
||||
@ -44,7 +47,9 @@ sending a mail to <afl-users+subscribe@googlegroups.com>.
|
||||
- Unicornafl
|
||||
- Added powerPC support from unicorn/next
|
||||
- rust bindings!
|
||||
- Allow running in /tmp (only unsafe with umask 0)
|
||||
- we moved radamsa to be a custom mutator in ./custom_mutators/. It is not
|
||||
compiled by default anymore.
|
||||
- allow running in /tmp (only unsafe with umask 0)
|
||||
- persistent mode shared memory testcase handover (instead of via
|
||||
files/stdin) - 10-100% performance increase
|
||||
- General support for 64 bit PowerPC, RiscV, Sparc etc.
|
||||
|
||||
@ -1,9 +0,0 @@
|
||||
# libradamsa
|
||||
|
||||
Pretranslated radamsa library. This code belongs to the radamsa author.
|
||||
|
||||
> Original repository: https://gitlab.com/akihe/radamsa
|
||||
|
||||
> Source commit: 7b2cc2d0
|
||||
|
||||
> The code here is adapted for AFL++ with minor changes respect the original version
|
||||
@ -21,6 +21,7 @@ We find that AFL's exploitation-based constant schedule assigns **too much energ
|
||||
| `-p exploit` (AFL) | 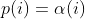 |
|
||||
| `-p mmopt` | Experimental: `explore` with no weighting to runtime and increased weighting on the last 5 queue entries |
|
||||
| `-p rare` | Experimental: `rare` puts focus on queue entries that hit rare edges |
|
||||
| `-p seek` | Experimental: `seek` is EXPLORE but ignoring the runtime of the queue input and less focus on the size |
|
||||
where *α(i)* is the performance score that AFL uses to compute for the seed input *i*, *β(i)>1* is a constant, *s(i)* is the number of times that seed *i* has been chosen from the queue, *f(i)* is the number of generated inputs that exercise the same path as seed *i*, and *μ* is the average number of generated inputs exercising a path.
|
||||
|
||||
More details can be found in the paper that was accepted at the [23rd ACM Conference on Computer and Communications Security (CCS'16)](https://www.sigsac.org/ccs/CCS2016/accepted-papers/).
|
||||
|
||||
@ -28,11 +28,12 @@ MAN_PATH ?= $(PREFIX)/man/man8
|
||||
|
||||
VERSION = $(shell grep '^$(HASH)define VERSION ' ../config.h | cut -d '"' -f2)
|
||||
|
||||
CFLAGS ?= -O3 -g -funroll-loops -D_FORTIFY_SOURCE=2
|
||||
CFLAGS = -Wall -I../include -Wno-pointer-sign \
|
||||
-DAFL_PATH=\"$(HELPER_PATH)\" -DBIN_PATH=\"$(BIN_PATH)\" \
|
||||
-DGCC_VERSION=\"$(GCCVER)\" -DGCC_BINDIR=\"$(GCCBINDIR)\" \
|
||||
-Wno-unused-function
|
||||
CFLAGS ?= -O3 -g -funroll-loops -D_FORTIFY_SOURCE=2
|
||||
CFLAGS_SAFE := -Wall -I../include -Wno-pointer-sign \
|
||||
-DAFL_PATH=\"$(HELPER_PATH)\" -DBIN_PATH=\"$(BIN_PATH)\" \
|
||||
-DGCC_VERSION=\"$(GCCVER)\" -DGCC_BINDIR=\"$(GCCBINDIR)\" \
|
||||
-Wno-unused-function
|
||||
override CFLAGS += $(CFLAGS_SAFE)
|
||||
|
||||
CXXFLAGS ?= -O3 -g -funroll-loops -D_FORTIFY_SOURCE=2
|
||||
CXXEFLAGS := $(CXXFLAGS) -Wall
|
||||
@ -60,12 +61,12 @@ ifeq "$(shell echo '$(HASH)include <sys/ipc.h>@$(HASH)include <sys/shm.h>@int ma
|
||||
SHMAT_OK=1
|
||||
else
|
||||
SHMAT_OK=0
|
||||
CFLAGS+=-DUSEMMAP=1
|
||||
override CFLAGS += -DUSEMMAP=1
|
||||
endif
|
||||
|
||||
ifeq "$(TEST_MMAP)" "1"
|
||||
SHMAT_OK=0
|
||||
CFLAGS+=-DUSEMMAP=1
|
||||
override CFLAGS += -DUSEMMAP=1
|
||||
endif
|
||||
|
||||
ifneq "$(shell uname -s)" "Haiku"
|
||||
@ -113,7 +114,7 @@ afl-common.o: ../src/afl-common.c
|
||||
$(CXX) $(CXXEFLAGS) $(PLUGIN_FLAGS) -shared $< -o $@
|
||||
|
||||
../afl-gcc-rt.o: afl-gcc-rt.o.c | test_deps
|
||||
$(CC) $(CFLAGS) -fPIC -c $< -o $@
|
||||
$(CC) $(CFLAGS_SAFE) -fPIC -c $< -o $@
|
||||
|
||||
test_build: $(PROGS)
|
||||
@echo "[*] Testing the CC wrapper and instrumentation output..."
|
||||
|
||||
@ -188,10 +188,11 @@ enum {
|
||||
/* 15 */ STAGE_HAVOC,
|
||||
/* 16 */ STAGE_SPLICE,
|
||||
/* 17 */ STAGE_PYTHON,
|
||||
/* 18 */ STAGE_RADAMSA,
|
||||
/* 19 */ STAGE_CUSTOM_MUTATOR,
|
||||
/* 20 */ STAGE_COLORIZATION,
|
||||
/* 21 */ STAGE_ITS,
|
||||
/* 18 */ STAGE_CUSTOM_MUTATOR,
|
||||
/* 19 */ STAGE_COLORIZATION,
|
||||
/* 20 */ STAGE_ITS,
|
||||
|
||||
STAGE_NUM_MAX
|
||||
|
||||
};
|
||||
|
||||
@ -233,6 +234,7 @@ enum {
|
||||
/* 05 */ QUAD, /* Quadratic schedule */
|
||||
/* 06 */ RARE, /* Rare edges */
|
||||
/* 07 */ MMOPT, /* Modified MOPT schedule */
|
||||
/* 08 */ SEEK, /* EXPLORE that ignores timings */
|
||||
|
||||
POWER_SCHEDULES_NUM
|
||||
|
||||
@ -426,9 +428,6 @@ typedef struct afl_state {
|
||||
u8 schedule; /* Power schedule (default: EXPLORE)*/
|
||||
u8 havoc_max_mult;
|
||||
|
||||
u8 use_radamsa;
|
||||
size_t (*radamsa_mutate_ptr)(u8 *, size_t, u8 *, size_t, u32);
|
||||
|
||||
u8 skip_deterministic, /* Skip deterministic stages? */
|
||||
use_splicing, /* Recombine input files? */
|
||||
non_instrumented_mode, /* Run in non-instrumented mode? */
|
||||
|
||||
@ -40,8 +40,8 @@
|
||||
#if (defined(__linux__) && !defined(__ANDROID__)) || defined(__HAIKU__)
|
||||
#include <unistd.h>
|
||||
#ifdef __linux__
|
||||
#include <sys/syscall.h>
|
||||
#include <malloc.h>
|
||||
#include <sys/syscall.h>
|
||||
#include <malloc.h>
|
||||
#endif
|
||||
#ifdef __NR_getrandom
|
||||
#define arc4random_buf(p, l) \
|
||||
|
||||
@ -33,7 +33,7 @@
|
||||
#include "../types.h"
|
||||
#include "../config.h"
|
||||
|
||||
#if !defined __linux__ && !defined __APPLE__ && !defined __FreeBSD__ && \
|
||||
#if !defined __linux__ && !defined __APPLE__ && !defined __FreeBSD__ && \
|
||||
!defined __OpenBSD__ && !defined __NetBSD__ && !defined __DragonFly__ && \
|
||||
!defined(__HAIKU__)
|
||||
#error "Sorry, this library is unsupported in this platform for now!"
|
||||
@ -233,18 +233,19 @@ static void __tokencap_load_mappings(void) {
|
||||
}
|
||||
|
||||
munmap(buf, len);
|
||||
#elif defined __HAIKU__
|
||||
#elif defined __HAIKU__
|
||||
image_info ii;
|
||||
int32_t group = 0;
|
||||
int32_t group = 0;
|
||||
|
||||
while (get_next_image_info(0, &group, &ii) == B_OK) {
|
||||
|
||||
__tokencap_ro[__tokencap_ro_cnt].st = ii.text;
|
||||
__tokencap_ro[__tokencap_ro_cnt].en = ((char *)ii.text) + ii.text_size;
|
||||
__tokencap_ro[__tokencap_ro_cnt].st = ii.text;
|
||||
__tokencap_ro[__tokencap_ro_cnt].en = ((char *)ii.text) + ii.text_size;
|
||||
|
||||
if (++__tokencap_ro_cnt == MAX_MAPPINGS) break;
|
||||
if (++__tokencap_ro_cnt == MAX_MAPPINGS) break;
|
||||
|
||||
}
|
||||
|
||||
#endif
|
||||
|
||||
}
|
||||
|
||||
@ -196,20 +196,21 @@ ifeq "$(shell echo 'int main() {return 0; }' | $(CLANG_BIN) -x c - -fuse-ld=`com
|
||||
endif
|
||||
endif
|
||||
|
||||
CFLAGS ?= -O3 -funroll-loops -fpic -D_FORTIFY_SOURCE=2
|
||||
override CFLAGS += -Wall \
|
||||
-g -Wno-pointer-sign -I ../include/ \
|
||||
-DAFL_PATH=\"$(HELPER_PATH)\" -DBIN_PATH=\"$(BIN_PATH)\" \
|
||||
-DLLVM_BINDIR=\"$(LLVM_BINDIR)\" -DVERSION=\"$(VERSION)\" \
|
||||
-DLLVM_LIBDIR=\"$(LLVM_LIBDIR)\" -DLLVM_VERSION=\"$(LLVMVER)\" \
|
||||
-DAFL_CLANG_FLTO=\"$(AFL_CLANG_FLTO)\" \
|
||||
-DAFL_REAL_LD=\"$(AFL_REAL_LD)\" -DAFL_CLANG_FUSELD=\"$(AFL_CLANG_FUSELD)\" \
|
||||
-DCLANG_BIN=\"$(CLANG_BIN)\" -DCLANGPP_BIN=\"$(CLANGPP_BIN)\" -DUSE_BINDIR=$(USE_BINDIR) -Wno-unused-function
|
||||
CFLAGS ?= -O3 -funroll-loops -fPIC -D_FORTIFY_SOURCE=2
|
||||
CFLAGS_SAFE := -Wall -g -Wno-pointer-sign -I ../include/ \
|
||||
-DAFL_PATH=\"$(HELPER_PATH)\" -DBIN_PATH=\"$(BIN_PATH)\" \
|
||||
-DLLVM_BINDIR=\"$(LLVM_BINDIR)\" -DVERSION=\"$(VERSION)\" \
|
||||
-DLLVM_LIBDIR=\"$(LLVM_LIBDIR)\" -DLLVM_VERSION=\"$(LLVMVER)\" \
|
||||
-DAFL_CLANG_FLTO=\"$(AFL_CLANG_FLTO)\" \
|
||||
-DAFL_REAL_LD=\"$(AFL_REAL_LD)\" -DAFL_CLANG_FUSELD=\"$(AFL_CLANG_FUSELD)\" \
|
||||
-DCLANG_BIN=\"$(CLANG_BIN)\" -DCLANGPP_BIN=\"$(CLANGPP_BIN)\" -DUSE_BINDIR=$(USE_BINDIR) -Wno-unused-function
|
||||
override CFLAGS += $(CFLAGS_SAFE)
|
||||
|
||||
ifdef AFL_TRACE_PC
|
||||
$(info Compile option AFL_TRACE_PC is deprecated, just set AFL_LLVM_INSTRUMENT=PCGUARD to activate when compiling targets )
|
||||
endif
|
||||
|
||||
CXXFLAGS ?= -O3 -funroll-loops -fpic -D_FORTIFY_SOURCE=2
|
||||
CXXFLAGS ?= -O3 -funroll-loops -fPIC -D_FORTIFY_SOURCE=2
|
||||
override CXXFLAGS += -Wall -g -I ../include/ \
|
||||
-DVERSION=\"$(VERSION)\" -Wno-variadic-macros
|
||||
|
||||
@ -219,7 +220,7 @@ endif
|
||||
ifneq "$(LLVM_CONFIG)" ""
|
||||
CLANG_CFL += -I$(shell dirname $(LLVM_CONFIG))/../include
|
||||
endif
|
||||
CLANG_CPPFL = `$(LLVM_CONFIG) --cxxflags` -fno-rtti -fpic $(CXXFLAGS)
|
||||
CLANG_CPPFL = `$(LLVM_CONFIG) --cxxflags` -fno-rtti -fPIC $(CXXFLAGS)
|
||||
CLANG_LFL = `$(LLVM_CONFIG) --ldflags` $(LDFLAGS)
|
||||
|
||||
|
||||
@ -344,9 +345,9 @@ endif
|
||||
../afl-llvm-lto-instrumentation.so: afl-llvm-lto-instrumentation.so.cc afl-llvm-common.o
|
||||
ifeq "$(LLVM_LTO)" "1"
|
||||
$(CXX) $(CLANG_CPPFL) -Wno-writable-strings -fno-rtti -fPIC -std=$(LLVM_STDCXX) -shared $< -o $@ $(CLANG_LFL) afl-llvm-common.o
|
||||
$(CLANG_BIN) $(CFLAGS) -Wno-unused-result -O0 $(AFL_CLANG_FLTO) -fPIC -c afl-llvm-rt-lto.o.c -o ../afl-llvm-rt-lto.o
|
||||
@$(CLANG_BIN) $(CFLAGS) -Wno-unused-result -O0 $(AFL_CLANG_FLTO) -m64 -fPIC -c afl-llvm-rt-lto.o.c -o ../afl-llvm-rt-lto-64.o 2>/dev/null; if [ "$$?" = "0" ]; then : ; fi
|
||||
@$(CLANG_BIN) $(CFLAGS) -Wno-unused-result -O0 $(AFL_CLANG_FLTO) -m32 -fPIC -c afl-llvm-rt-lto.o.c -o ../afl-llvm-rt-lto-32.o 2>/dev/null; if [ "$$?" = "0" ]; then : ; fi
|
||||
$(CLANG_BIN) $(CFLAGS_SAFE) -Wno-unused-result -O0 $(AFL_CLANG_FLTO) -fPIC -c afl-llvm-rt-lto.o.c -o ../afl-llvm-rt-lto.o
|
||||
@$(CLANG_BIN) $(CFLAGS_SAFE) -Wno-unused-result -O0 $(AFL_CLANG_FLTO) -m64 -fPIC -c afl-llvm-rt-lto.o.c -o ../afl-llvm-rt-lto-64.o 2>/dev/null; if [ "$$?" = "0" ]; then : ; fi
|
||||
@$(CLANG_BIN) $(CFLAGS_SAFE) -Wno-unused-result -O0 $(AFL_CLANG_FLTO) -m32 -fPIC -c afl-llvm-rt-lto.o.c -o ../afl-llvm-rt-lto-32.o 2>/dev/null; if [ "$$?" = "0" ]; then : ; fi
|
||||
endif
|
||||
|
||||
../afl-llvm-lto-instrim.so: afl-llvm-lto-instrim.so.cc afl-llvm-common.o
|
||||
@ -370,20 +371,20 @@ endif
|
||||
$(CXX) $(CLANG_CPPFL) -shared $< -o $@ $(CLANG_LFL) afl-llvm-common.o
|
||||
|
||||
document:
|
||||
$(CLANG_BIN) -D_AFL_DOCUMENT_MUTATIONS $(CFLAGS) -Wno-unused-result -fPIC -c afl-llvm-rt.o.c -o ../afl-llvm-rt.o
|
||||
@$(CLANG_BIN) -D_AFL_DOCUMENT_MUTATIONS $(CFLAGS) -Wno-unused-result -m32 -fPIC -c afl-llvm-rt.o.c -o ../afl-llvm-rt-32.o 2>/dev/null; if [ "$$?" = "0" ]; then echo "success!"; else echo "failed (that's fine)"; fi
|
||||
@$(CLANG_BIN) -D_AFL_DOCUMENT_MUTATIONS $(CFLAGS) -Wno-unused-result -m64 -fPIC -c afl-llvm-rt.o.c -o ../afl-llvm-rt-64.o 2>/dev/null; if [ "$$?" = "0" ]; then echo "success!"; else echo "failed (that's fine)"; fi
|
||||
$(CLANG_BIN) -D_AFL_DOCUMENT_MUTATIONS $(CFLAGS_SAFE) -O3 -Wno-unused-result -fPIC -c afl-llvm-rt.o.c -o ../afl-llvm-rt.o
|
||||
@$(CLANG_BIN) -D_AFL_DOCUMENT_MUTATIONS $(CFLAGS_SAFE) -O3 -Wno-unused-result -m32 -fPIC -c afl-llvm-rt.o.c -o ../afl-llvm-rt-32.o 2>/dev/null; if [ "$$?" = "0" ]; then echo "success!"; else echo "failed (that's fine)"; fi
|
||||
@$(CLANG_BIN) -D_AFL_DOCUMENT_MUTATIONS $(CFLAGS_SAFE) -O3 -Wno-unused-result -m64 -fPIC -c afl-llvm-rt.o.c -o ../afl-llvm-rt-64.o 2>/dev/null; if [ "$$?" = "0" ]; then echo "success!"; else echo "failed (that's fine)"; fi
|
||||
|
||||
../afl-llvm-rt.o: afl-llvm-rt.o.c | test_deps
|
||||
$(CLANG_BIN) $(CFLAGS) -Wno-unused-result -fPIC -c $< -o $@
|
||||
$(CLANG_BIN) $(CFLAGS_SAFE) -O3 -Wno-unused-result -fPIC -c $< -o $@
|
||||
|
||||
../afl-llvm-rt-32.o: afl-llvm-rt.o.c | test_deps
|
||||
@printf "[*] Building 32-bit variant of the runtime (-m32)... "
|
||||
@$(CLANG_BIN) $(CFLAGS) -Wno-unused-result -m32 -fPIC -c $< -o $@ 2>/dev/null; if [ "$$?" = "0" ]; then echo "success!"; else echo "failed (that's fine)"; fi
|
||||
@$(CLANG_BIN) $(CFLAGS_SAFE) -O3 -Wno-unused-result -m32 -fPIC -c $< -o $@ 2>/dev/null; if [ "$$?" = "0" ]; then echo "success!"; else echo "failed (that's fine)"; fi
|
||||
|
||||
../afl-llvm-rt-64.o: afl-llvm-rt.o.c | test_deps
|
||||
@printf "[*] Building 64-bit variant of the runtime (-m64)... "
|
||||
@$(CLANG_BIN) $(CFLAGS) -Wno-unused-result -m64 -fPIC -c $< -o $@ 2>/dev/null; if [ "$$?" = "0" ]; then echo "success!"; else echo "failed (that's fine)"; fi
|
||||
@$(CLANG_BIN) $(CFLAGS_SAFE) -O3 -Wno-unused-result -m64 -fPIC -c $< -o $@ 2>/dev/null; if [ "$$?" = "0" ]; then echo "success!"; else echo "failed (that's fine)"; fi
|
||||
|
||||
test_build: $(PROGS)
|
||||
@echo "[*] Testing the CC wrapper and instrumentation output..."
|
||||
|
||||
@ -103,6 +103,7 @@ struct InsTrim : public ModulePass {
|
||||
bool runOnModule(Module &M) override {
|
||||
|
||||
char be_quiet = 0;
|
||||
setvbuf(stdout, NULL, _IONBF, 0);
|
||||
|
||||
if ((isatty(2) && !getenv("AFL_QUIET")) || getenv("AFL_DEBUG") != NULL) {
|
||||
|
||||
|
||||
@ -113,6 +113,8 @@ struct InsTrimLTO : public ModulePass {
|
||||
char be_quiet = 0;
|
||||
char *ptr;
|
||||
|
||||
setvbuf(stdout, NULL, _IONBF, 0);
|
||||
|
||||
if ((isatty(2) && !getenv("AFL_QUIET")) || getenv("AFL_DEBUG") != NULL) {
|
||||
|
||||
SAYF(cCYA "InsTrimLTO" VERSION cRST
|
||||
|
||||
@ -109,6 +109,7 @@ bool AFLLTOPass::runOnModule(Module &M) {
|
||||
IntegerType *Int64Ty = IntegerType::getInt64Ty(C);
|
||||
|
||||
/* Show a banner */
|
||||
setvbuf(stdout, NULL, _IONBF, 0);
|
||||
|
||||
if ((isatty(2) && !getenv("AFL_QUIET")) || debug) {
|
||||
|
||||
@ -162,7 +163,7 @@ bool AFLLTOPass::runOnModule(Module &M) {
|
||||
|
||||
}
|
||||
|
||||
if (debug) { fprintf(stderr, "map address is %lu\n", map_addr); }
|
||||
if (debug) { fprintf(stderr, "map address is 0x%lx\n", map_addr); }
|
||||
|
||||
/* Get/set the globals for the SHM region. */
|
||||
|
||||
|
||||
@ -111,6 +111,7 @@ bool AFLwhitelist::runOnModule(Module &M) {
|
||||
/* Show a banner */
|
||||
|
||||
char be_quiet = 0;
|
||||
setvbuf(stdout, NULL, _IONBF, 0);
|
||||
|
||||
if ((isatty(2) && !getenv("AFL_QUIET")) || getenv("AFL_DEBUG") != NULL) {
|
||||
|
||||
|
||||
@ -140,6 +140,7 @@ bool AFLCoverage::runOnModule(Module &M) {
|
||||
/* Show a banner */
|
||||
|
||||
char be_quiet = 0;
|
||||
setvbuf(stdout, NULL, _IONBF, 0);
|
||||
|
||||
if (getenv("AFL_DEBUG")) debug = 1;
|
||||
|
||||
|
||||
@ -44,7 +44,7 @@ void setup_custom_mutators(afl_state_t *afl) {
|
||||
FATAL(
|
||||
"MOpt and custom mutator are mutually exclusive. We accept pull "
|
||||
"requests that integrates MOpt with the optional mutators "
|
||||
"(custom/radamsa/redqueen/...).");
|
||||
"(custom/redqueen/...).");
|
||||
|
||||
u8 *fn_token = (u8 *)strsep((char **)&fn, ";:,");
|
||||
|
||||
@ -89,7 +89,7 @@ void setup_custom_mutators(afl_state_t *afl) {
|
||||
FATAL(
|
||||
"MOpt and Python mutator are mutually exclusive. We accept pull "
|
||||
"requests that integrates MOpt with the optional mutators "
|
||||
"(custom/radamsa/redqueen/...).");
|
||||
"(custom/redqueen/...).");
|
||||
|
||||
}
|
||||
|
||||
|
||||
@ -554,8 +554,6 @@ u8 fuzz_one_original(afl_state_t *afl) {
|
||||
|
||||
if (unlikely(perf_score == 0)) { goto abandon_entry; }
|
||||
|
||||
if (unlikely(afl->use_radamsa > 1)) { goto radamsa_stage; }
|
||||
|
||||
if (afl->shm.cmplog_mode && !afl->queue_cur->fully_colorized) {
|
||||
|
||||
if (input_to_state_stage(afl, in_buf, out_buf, len,
|
||||
@ -1685,6 +1683,7 @@ custom_mutator_stage:
|
||||
|
||||
retry_external_pick:
|
||||
/* Pick a random other queue entry for passing to external API */
|
||||
|
||||
do {
|
||||
|
||||
tid = rand_below(afl, afl->queued_paths);
|
||||
@ -1709,7 +1708,7 @@ custom_mutator_stage:
|
||||
/* Make sure that the target has a reasonable length. */
|
||||
|
||||
while (target && (target->len < 2 || target == afl->queue_cur) &&
|
||||
afl->queued_paths > 1) {
|
||||
afl->queued_paths > 3) {
|
||||
|
||||
target = target->next;
|
||||
++afl->splicing_with;
|
||||
@ -2426,63 +2425,6 @@ retry_splicing:
|
||||
#endif /* !IGNORE_FINDS */
|
||||
|
||||
ret_val = 0;
|
||||
goto radamsa_stage;
|
||||
|
||||
radamsa_stage:
|
||||
|
||||
if (likely(!afl->use_radamsa || !afl->radamsa_mutate_ptr)) {
|
||||
|
||||
goto abandon_entry;
|
||||
|
||||
}
|
||||
|
||||
afl->stage_name = "radamsa";
|
||||
afl->stage_short = "radamsa";
|
||||
afl->stage_max = (HAVOC_CYCLES * perf_score / afl->havoc_div / 100)
|
||||
<< afl->use_radamsa;
|
||||
|
||||
if (afl->stage_max < HAVOC_MIN) { afl->stage_max = HAVOC_MIN; }
|
||||
|
||||
orig_hit_cnt = afl->queued_paths + afl->unique_crashes;
|
||||
|
||||
/* Read the additional testcase.
|
||||
We'll reuse in_scratch, as it is free at this point.
|
||||
*/
|
||||
u8 *save_buf = ck_maybe_grow(BUF_PARAMS(in_scratch), len);
|
||||
memcpy(save_buf, out_buf, len);
|
||||
|
||||
u32 max_len = len + choose_block_len(afl, HAVOC_BLK_XL);
|
||||
u8 *new_buf = ck_maybe_grow(BUF_PARAMS(out_scratch), max_len);
|
||||
u8 *tmp_buf;
|
||||
|
||||
for (afl->stage_cur = 0; afl->stage_cur < afl->stage_max; ++afl->stage_cur) {
|
||||
|
||||
u32 new_len = afl->radamsa_mutate_ptr(save_buf, len, new_buf, max_len,
|
||||
rand_get_seed(afl));
|
||||
|
||||
if (new_len) {
|
||||
|
||||
temp_len = new_len;
|
||||
tmp_buf = new_buf;
|
||||
|
||||
} else {
|
||||
|
||||
tmp_buf = save_buf; // nope but I dont care
|
||||
temp_len = len;
|
||||
|
||||
}
|
||||
|
||||
if (common_fuzz_stuff(afl, tmp_buf, temp_len)) { goto abandon_entry; }
|
||||
|
||||
}
|
||||
|
||||
new_hit_cnt = afl->queued_paths + afl->unique_crashes;
|
||||
|
||||
afl->stage_finds[STAGE_RADAMSA] += new_hit_cnt - orig_hit_cnt;
|
||||
afl->stage_cycles[STAGE_RADAMSA] += afl->stage_max;
|
||||
|
||||
ret_val = 0;
|
||||
goto abandon_entry;
|
||||
|
||||
/* we are through with this queue entry - for this iteration */
|
||||
abandon_entry:
|
||||
|
||||
@ -201,8 +201,7 @@ void update_bitmap_score(afl_state_t *afl, struct queue_entry *q) {
|
||||
else
|
||||
fuzz_p2 = q->fuzz_level;
|
||||
|
||||
if (unlikely(afl->schedule == MMOPT || afl->schedule == RARE) ||
|
||||
unlikely(afl->fixed_seed)) {
|
||||
if (unlikely(afl->schedule >= RARE) || unlikely(afl->fixed_seed)) {
|
||||
|
||||
fav_factor = q->len << 2;
|
||||
|
||||
@ -228,8 +227,7 @@ void update_bitmap_score(afl_state_t *afl, struct queue_entry *q) {
|
||||
else
|
||||
top_rated_fuzz_p2 = afl->top_rated[i]->fuzz_level;
|
||||
|
||||
if (unlikely(afl->schedule == MMOPT || afl->schedule == RARE) ||
|
||||
unlikely(afl->fixed_seed)) {
|
||||
if (unlikely(afl->schedule >= RARE) || unlikely(afl->fixed_seed)) {
|
||||
|
||||
top_rated_fav_factor = afl->top_rated[i]->len << 2;
|
||||
|
||||
@ -250,8 +248,7 @@ void update_bitmap_score(afl_state_t *afl, struct queue_entry *q) {
|
||||
|
||||
}
|
||||
|
||||
if (unlikely(afl->schedule == MMOPT || afl->schedule == RARE) ||
|
||||
unlikely(afl->fixed_seed)) {
|
||||
if (unlikely(afl->schedule >= RARE) || unlikely(afl->fixed_seed)) {
|
||||
|
||||
if (fav_factor > afl->top_rated[i]->len << 2) { continue; }
|
||||
|
||||
@ -396,8 +393,7 @@ u32 calculate_score(afl_state_t *afl, struct queue_entry *q) {
|
||||
// Longer execution time means longer work on the input, the deeper in
|
||||
// coverage, the better the fuzzing, right? -mh
|
||||
|
||||
if (afl->schedule != MMOPT && afl->schedule != RARE &&
|
||||
likely(!afl->fixed_seed)) {
|
||||
if (afl->schedule >= RARE && likely(!afl->fixed_seed)) {
|
||||
|
||||
if (q->exec_us * 0.1 > avg_exec_us) {
|
||||
|
||||
@ -509,6 +505,9 @@ u32 calculate_score(afl_state_t *afl, struct queue_entry *q) {
|
||||
case EXPLORE:
|
||||
break;
|
||||
|
||||
case SEEK:
|
||||
break;
|
||||
|
||||
case EXPLOIT:
|
||||
factor = MAX_FACTOR;
|
||||
break;
|
||||
|
||||
@ -286,12 +286,6 @@ u8 calibrate_case(afl_state_t *afl, struct queue_entry *q, u8 *use_mem,
|
||||
|
||||
u64 cksum;
|
||||
|
||||
if (!first_run && !(afl->stage_cur % afl->stats_update_freq)) {
|
||||
|
||||
show_stats(afl);
|
||||
|
||||
}
|
||||
|
||||
write_to_testcase(afl, use_mem, q->len);
|
||||
|
||||
fault = fuzz_run_target(afl, &afl->fsrv, use_tmout);
|
||||
@ -374,6 +368,8 @@ u8 calibrate_case(afl_state_t *afl, struct queue_entry *q, u8 *use_mem,
|
||||
|
||||
abort_calibration:
|
||||
|
||||
if (q->cal_failed) { q->exec_cksum = 0; }
|
||||
|
||||
if (new_bits == 2 && !q->has_new_cov) {
|
||||
|
||||
q->has_new_cov = 1;
|
||||
@ -466,6 +462,12 @@ void sync_fuzzers(afl_state_t *afl) {
|
||||
|
||||
synced++;
|
||||
|
||||
/* document the attempt to sync to this instance */
|
||||
|
||||
sprintf(qd_synced_path, "%s/.synced/%s.last", afl->out_dir, sd_ent->d_name);
|
||||
id_fd = open(qd_synced_path, O_RDWR | O_CREAT | O_TRUNC, 0600);
|
||||
if (id_fd >= 0) close(id_fd);
|
||||
|
||||
/* Skip anything that doesn't have a queue/ subdirectory. */
|
||||
|
||||
sprintf(qd_path, "%s/%s/queue", afl->sync_dir, sd_ent->d_name);
|
||||
@ -490,14 +492,13 @@ void sync_fuzzers(afl_state_t *afl) {
|
||||
|
||||
if (id_fd < 0) { PFATAL("Unable to create '%s'", qd_synced_path); }
|
||||
|
||||
if (read(id_fd, &min_accept, sizeof(u32)) > 0) {
|
||||
if (read(id_fd, &min_accept, sizeof(u32)) == sizeof(u32)) {
|
||||
|
||||
next_min_accept = min_accept;
|
||||
lseek(id_fd, 0, SEEK_SET);
|
||||
|
||||
}
|
||||
|
||||
next_min_accept = min_accept;
|
||||
|
||||
/* Show stats */
|
||||
|
||||
snprintf(afl->stage_name_buf, STAGE_BUF_SIZE, "sync %u", ++sync_cnt);
|
||||
|
||||
@ -30,9 +30,9 @@ s8 interesting_8[] = {INTERESTING_8};
|
||||
s16 interesting_16[] = {INTERESTING_8, INTERESTING_16};
|
||||
s32 interesting_32[] = {INTERESTING_8, INTERESTING_16, INTERESTING_32};
|
||||
|
||||
char *power_names[POWER_SCHEDULES_NUM] = {
|
||||
|
||||
"explore", "exploit", "fast", "coe", "lin", "quad", "rare", "mmopt"};
|
||||
char *power_names[POWER_SCHEDULES_NUM] = {"explore", "exploit", "fast",
|
||||
"coe", "lin", "quad",
|
||||
"rare", "mmopt", "seek"};
|
||||
|
||||
/* Initialize MOpt "globals" for this afl state */
|
||||
|
||||
|
||||
@ -194,7 +194,8 @@ void maybe_update_plot_file(afl_state_t *afl, double bitmap_cvg, double eps) {
|
||||
afl->plot_prev_uc == afl->unique_crashes &&
|
||||
afl->plot_prev_uh == afl->unique_hangs &&
|
||||
afl->plot_prev_md == afl->max_depth) ||
|
||||
unlikely(!afl->queue_cycle)) {
|
||||
unlikely(!afl->queue_cycle) ||
|
||||
unlikely(get_cur_time() - afl->start_time <= 60)) {
|
||||
|
||||
return;
|
||||
|
||||
@ -745,15 +746,13 @@ void show_stats(afl_state_t *afl) {
|
||||
afl->sync_id ? u_stringify_int(IB(0), afl->queued_imported)
|
||||
: (u8 *)"n/a");
|
||||
|
||||
sprintf(tmp, "%s/%s, %s/%s, %s/%s",
|
||||
sprintf(tmp, "%s/%s, %s/%s",
|
||||
u_stringify_int(IB(0), afl->stage_finds[STAGE_HAVOC]),
|
||||
u_stringify_int(IB(2), afl->stage_cycles[STAGE_HAVOC]),
|
||||
u_stringify_int(IB(3), afl->stage_finds[STAGE_SPLICE]),
|
||||
u_stringify_int(IB(4), afl->stage_cycles[STAGE_SPLICE]),
|
||||
u_stringify_int(IB(5), afl->stage_finds[STAGE_RADAMSA]),
|
||||
u_stringify_int(IB(6), afl->stage_cycles[STAGE_RADAMSA]));
|
||||
u_stringify_int(IB(4), afl->stage_cycles[STAGE_SPLICE]));
|
||||
|
||||
SAYF(bV bSTOP " havoc/rad : " cRST "%-36s " bSTG bV bSTOP, tmp);
|
||||
SAYF(bV bSTOP "havoc/splice : " cRST "%-36s " bSTG bV bSTOP, tmp);
|
||||
|
||||
if (t_bytes) {
|
||||
|
||||
@ -834,18 +833,19 @@ void show_stats(afl_state_t *afl) {
|
||||
|
||||
}
|
||||
|
||||
if (afl->custom_mutators_count) {
|
||||
// if (afl->custom_mutators_count) {
|
||||
|
||||
sprintf(tmp, "%s/%s",
|
||||
u_stringify_int(IB(0), afl->stage_finds[STAGE_CUSTOM_MUTATOR]),
|
||||
u_stringify_int(IB(1), afl->stage_cycles[STAGE_CUSTOM_MUTATOR]));
|
||||
SAYF(bV bSTOP " custom mut. : " cRST "%-36s " bSTG bV RESET_G1, tmp);
|
||||
//
|
||||
// sprintf(tmp, "%s/%s",
|
||||
// u_stringify_int(IB(0), afl->stage_finds[STAGE_CUSTOM_MUTATOR]),
|
||||
// u_stringify_int(IB(1), afl->stage_cycles[STAGE_CUSTOM_MUTATOR]));
|
||||
// SAYF(bV bSTOP " custom mut. : " cRST "%-36s " bSTG bV RESET_G1, tmp);
|
||||
//
|
||||
//} else {
|
||||
|
||||
} else {
|
||||
SAYF(bV bSTOP " trim : " cRST "%-36s " bSTG bV RESET_G1, tmp);
|
||||
|
||||
SAYF(bV bSTOP " trim : " cRST "%-36s " bSTG bV RESET_G1, tmp);
|
||||
|
||||
}
|
||||
//}
|
||||
|
||||
/* Provide some CPU utilization stats. */
|
||||
|
||||
|
||||
167
src/afl-fuzz.c
167
src/afl-fuzz.c
@ -46,63 +46,6 @@ static void at_exit() {
|
||||
|
||||
}
|
||||
|
||||
static u8 *get_libradamsa_path(u8 *own_loc) {
|
||||
|
||||
u8 *tmp, *cp, *rsl, *own_copy;
|
||||
|
||||
tmp = getenv("AFL_PATH");
|
||||
|
||||
if (tmp) {
|
||||
|
||||
cp = alloc_printf("%s/libradamsa.so", tmp);
|
||||
|
||||
if (access(cp, X_OK)) { FATAL("Unable to find '%s'", cp); }
|
||||
|
||||
return cp;
|
||||
|
||||
}
|
||||
|
||||
own_copy = ck_strdup(own_loc);
|
||||
rsl = strrchr(own_copy, '/');
|
||||
|
||||
if (rsl) {
|
||||
|
||||
*rsl = 0;
|
||||
|
||||
cp = alloc_printf("%s/libradamsa.so", own_copy);
|
||||
ck_free(own_copy);
|
||||
|
||||
if (!access(cp, X_OK)) { return cp; }
|
||||
|
||||
} else {
|
||||
|
||||
ck_free(own_copy);
|
||||
|
||||
}
|
||||
|
||||
if (!access(AFL_PATH "/libradamsa.so", X_OK)) {
|
||||
|
||||
return ck_strdup(AFL_PATH "/libradamsa.so");
|
||||
|
||||
}
|
||||
|
||||
if (!access(BIN_PATH "/libradamsa.so", X_OK)) {
|
||||
|
||||
return ck_strdup(BIN_PATH "/libradamsa.so");
|
||||
|
||||
}
|
||||
|
||||
SAYF(
|
||||
"\n" cLRD "[-] " cRST
|
||||
"Oops, unable to find the 'libradamsa.so' binary. The binary must be "
|
||||
"built\n"
|
||||
" separately using 'make radamsa'. If you already have the binary "
|
||||
"installed,\n you may need to specify AFL_PATH in the environment.\n");
|
||||
|
||||
FATAL("Failed to locate 'libradamsa.so'.");
|
||||
|
||||
}
|
||||
|
||||
/* Display usage hints. */
|
||||
|
||||
static void usage(afl_state_t *afl, u8 *argv0, int more_help) {
|
||||
@ -115,12 +58,13 @@ static void usage(afl_state_t *afl, u8 *argv0, int more_help) {
|
||||
" -o dir - output directory for fuzzer findings\n\n"
|
||||
|
||||
"Execution control settings:\n"
|
||||
" -p schedule - power schedules recompute a seed's performance "
|
||||
"score.\n"
|
||||
" <explore(default), fast, coe, lin, quad, exploit, "
|
||||
"mmopt, rare>\n"
|
||||
" -p schedule - power schedules compute a seed's performance score. "
|
||||
"<explore\n"
|
||||
" (default), fast, coe, lin, quad, exploit, mmopt, "
|
||||
"rare, seek>\n"
|
||||
" see docs/power_schedules.md\n"
|
||||
" -f file - location read by the fuzzed program (stdin)\n"
|
||||
" -f file - location read by the fuzzed program (default: stdin "
|
||||
"or @@)\n"
|
||||
" -t msec - timeout for each run (auto-scaled, 50-%d ms)\n"
|
||||
" -m megs - memory limit for child process (%d MB)\n"
|
||||
" -Q - use binary-only instrumentation (QEMU mode)\n"
|
||||
@ -129,8 +73,6 @@ static void usage(afl_state_t *afl, u8 *argv0, int more_help) {
|
||||
"mode)\n\n"
|
||||
|
||||
"Mutator settings:\n"
|
||||
" -R[R] - add Radamsa as mutator, add another -R to exclusivly "
|
||||
"run it\n"
|
||||
" -L minutes - use MOpt(imize) mode and set the time limit for "
|
||||
"entering the\n"
|
||||
" pacemaker mode (minutes of no new paths). 0 = "
|
||||
@ -146,7 +88,7 @@ static void usage(afl_state_t *afl, u8 *argv0, int more_help) {
|
||||
"devices etc.!)\n"
|
||||
" -d - quick & dirty mode (skips deterministic steps)\n"
|
||||
" -n - fuzz without instrumentation (non-instrumented mode)\n"
|
||||
" -x dir - optional fuzzer dictionary (see README.md, its really "
|
||||
" -x dict_file - optional fuzzer dictionary (see README.md, its really "
|
||||
"good!)\n\n"
|
||||
|
||||
"Testing settings:\n"
|
||||
@ -159,14 +101,16 @@ static void usage(afl_state_t *afl, u8 *argv0, int more_help) {
|
||||
|
||||
"Other stuff:\n"
|
||||
" -T text - text banner to show on the screen\n"
|
||||
" -M / -S id - distributed mode (see docs/parallel_fuzzing.md)\n"
|
||||
" -M/-S id - distributed mode (see docs/parallel_fuzzing.md)\n"
|
||||
" use -D to force -S secondary to perform deterministic "
|
||||
"fuzzing\n"
|
||||
" -I command - execute this command/script when a new crash is "
|
||||
"found\n"
|
||||
" -B bitmap.txt - mutate a specific test case, use the out/fuzz_bitmap "
|
||||
"file\n"
|
||||
//" -B bitmap.txt - mutate a specific test case, use the out/fuzz_bitmap
|
||||
//" "file\n"
|
||||
" -C - crash exploration mode (the peruvian rabbit thing)\n"
|
||||
" -e ext - file extension for the temporarily generated test "
|
||||
"case\n\n",
|
||||
" -e ext - file extension for the fuzz test case case (if "
|
||||
"needed)\n\n",
|
||||
argv0, EXEC_TIMEOUT, MEM_LIMIT);
|
||||
|
||||
if (more_help > 1) {
|
||||
@ -292,7 +236,7 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
rand_set_seed(afl, tv.tv_sec ^ tv.tv_usec ^ getpid());
|
||||
|
||||
while ((opt = getopt(argc, argv,
|
||||
"+c:i:I:o:f:m:t:T:dnCB:S:M:x:QNUWe:p:s:V:E:L:hRP:")) >
|
||||
"+c:i:I:o:f:m:t:T:dDnCB:S:M:x:QNUWe:p:s:V:E:L:hRP:")) >
|
||||
0) {
|
||||
|
||||
switch (opt) {
|
||||
@ -347,6 +291,10 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
|
||||
afl->schedule = RARE;
|
||||
|
||||
} else if (!stricmp(optarg, "seek")) {
|
||||
|
||||
afl->schedule = SEEK;
|
||||
|
||||
} else if (!stricmp(optarg, "explore") || !stricmp(optarg, "default") ||
|
||||
|
||||
!stricmp(optarg, "normal") || !stricmp(optarg, "afl")) {
|
||||
@ -384,7 +332,7 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
afl->out_dir = optarg;
|
||||
break;
|
||||
|
||||
case 'M': { /* master sync ID */
|
||||
case 'M': { /* main sync ID */
|
||||
|
||||
u8 *c;
|
||||
|
||||
@ -413,7 +361,7 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
|
||||
break;
|
||||
|
||||
case 'S':
|
||||
case 'S': /* secondary sync id */
|
||||
|
||||
if (afl->sync_id) { FATAL("Multiple -S or -M options not supported"); }
|
||||
afl->sync_id = ck_strdup(optarg);
|
||||
@ -518,6 +466,11 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
|
||||
break;
|
||||
|
||||
case 'D': /* enforce deterministic */
|
||||
|
||||
afl->skip_deterministic = 0;
|
||||
break;
|
||||
|
||||
case 'd': /* skip deterministic */
|
||||
|
||||
afl->skip_deterministic = 1;
|
||||
@ -782,15 +735,9 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
|
||||
case 'R':
|
||||
|
||||
if (afl->use_radamsa) {
|
||||
|
||||
afl->use_radamsa = 2;
|
||||
|
||||
} else {
|
||||
|
||||
afl->use_radamsa = 1;
|
||||
|
||||
}
|
||||
FATAL(
|
||||
"Radamsa is now a custom mutator, please use that "
|
||||
"(custom_mutators/radamsa/).");
|
||||
|
||||
break;
|
||||
|
||||
@ -833,47 +780,6 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
|
||||
}
|
||||
|
||||
if (afl->use_radamsa) {
|
||||
|
||||
if (afl->limit_time_sig > 0) {
|
||||
|
||||
FATAL(
|
||||
"MOpt and Radamsa are mutually exclusive unless you specify -L -1. "
|
||||
"We accept pull requests that integrates MOpt with the optional "
|
||||
"mutators (custom/radamsa/redqueen/...).");
|
||||
|
||||
}
|
||||
|
||||
if (afl->limit_time_sig && afl->use_radamsa > 1) {
|
||||
|
||||
FATAL("Radamsa in radamsa-only mode can not run together with -L");
|
||||
|
||||
}
|
||||
|
||||
OKF("Using Radamsa add-on");
|
||||
|
||||
u8 * libradamsa_path = get_libradamsa_path(argv[0]);
|
||||
void *handle = dlopen(libradamsa_path, RTLD_NOW);
|
||||
ck_free(libradamsa_path);
|
||||
|
||||
if (!handle) { FATAL("Failed to dlopen() libradamsa"); }
|
||||
|
||||
void (*radamsa_init_ptr)(void) = dlsym(handle, "radamsa_init");
|
||||
afl->radamsa_mutate_ptr = dlsym(handle, "radamsa");
|
||||
|
||||
if (!radamsa_init_ptr || !afl->radamsa_mutate_ptr) {
|
||||
|
||||
FATAL("Failed to dlsym() libradamsa");
|
||||
|
||||
}
|
||||
|
||||
/* radamsa_init installs some signal handlers, call it before
|
||||
setup_signal_handlers so that AFL++ can then replace those signal
|
||||
handlers */
|
||||
radamsa_init_ptr();
|
||||
|
||||
}
|
||||
|
||||
#if defined(__SANITIZE_ADDRESS__)
|
||||
if (afl->fsrv.mem_limit) {
|
||||
|
||||
@ -947,6 +853,9 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
case RARE:
|
||||
OKF("Using rare edge focus power schedule (RARE)");
|
||||
break;
|
||||
case SEEK:
|
||||
OKF("Using seek power schedule (SEEK)");
|
||||
break;
|
||||
case EXPLORE:
|
||||
OKF("Using exploration-based constant power schedule (EXPLORE, default)");
|
||||
break;
|
||||
@ -1093,7 +1002,7 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
|
||||
if (afl->is_main_node && check_main_node_exists(afl) == 1) {
|
||||
|
||||
WARNF("it is wasteful to run more than one master!");
|
||||
WARNF("it is wasteful to run more than one main node!");
|
||||
sleep(1);
|
||||
|
||||
}
|
||||
@ -1340,7 +1249,15 @@ int main(int argc, char **argv_orig, char **envp) {
|
||||
|
||||
if (!skipped_fuzz && !afl->stop_soon && afl->sync_id) {
|
||||
|
||||
if (!(sync_interval_cnt++ % SYNC_INTERVAL)) { sync_fuzzers(afl); }
|
||||
if (unlikely(afl->is_main_node)) {
|
||||
|
||||
if (!(sync_interval_cnt++ % (SYNC_INTERVAL / 2))) { sync_fuzzers(afl); }
|
||||
|
||||
} else {
|
||||
|
||||
if (!(sync_interval_cnt++ % SYNC_INTERVAL)) { sync_fuzzers(afl); }
|
||||
|
||||
}
|
||||
|
||||
}
|
||||
|
||||
|
||||
@ -36,7 +36,8 @@ static inline uint64_t rotl(const uint64_t x, int k) {
|
||||
void rand_set_seed(afl_state_t *afl, s64 init_seed) {
|
||||
|
||||
afl->init_seed = init_seed;
|
||||
afl->rand_seed[0] = hash64((void *)&afl->init_seed, sizeof(afl->init_seed), HASH_CONST);
|
||||
afl->rand_seed[0] =
|
||||
hash64((void *)&afl->init_seed, sizeof(afl->init_seed), HASH_CONST);
|
||||
afl->rand_seed[1] = afl->rand_seed[0] ^ 0x1234567890abcdef;
|
||||
afl->rand_seed[2] = afl->rand_seed[0] & 0x0123456789abcdef;
|
||||
afl->rand_seed[3] = afl->rand_seed[0] | 0x01abcde43f567908;
|
||||
|
||||
3
src/third_party/libradamsa/.gitignore
vendored
3
src/third_party/libradamsa/.gitignore
vendored
@ -1,3 +0,0 @@
|
||||
*.a
|
||||
*.o
|
||||
libradamsa-test
|
||||
75
src/third_party/libradamsa/libradamsa-test.c
vendored
75
src/third_party/libradamsa/libradamsa-test.c
vendored
@ -1,75 +0,0 @@
|
||||
#include <radamsa.h>
|
||||
#include <stdio.h>
|
||||
#include <inttypes.h>
|
||||
#include <string.h>
|
||||
#include <stdlib.h>
|
||||
#include <sys/mman.h>
|
||||
#include <sys/types.h>
|
||||
#include <fcntl.h>
|
||||
#include <unistd.h>
|
||||
#include <sys/stat.h>
|
||||
|
||||
size_t filesize(char* filename) {
|
||||
struct stat st;
|
||||
stat(filename, &st);
|
||||
return st.st_size;
|
||||
}
|
||||
|
||||
#define BUFSIZE 1024*1024
|
||||
|
||||
void fail(char *why) {
|
||||
printf("fail: %s\n", why);
|
||||
exit(1);
|
||||
}
|
||||
|
||||
void write_output(char *data, size_t len, int num) {
|
||||
char path[32];
|
||||
int fd;
|
||||
int wrote;
|
||||
sprintf(path, "/tmp/libradamsa-%d.fuzz", num);
|
||||
fd = open(path, O_WRONLY | O_CREAT | O_TRUNC, S_IRUSR | S_IWUSR);
|
||||
printf("Opened %s -> %d\n", path, fd);
|
||||
if (fd < 0) {
|
||||
fail("failed to open output file");
|
||||
}
|
||||
wrote = write(fd, data, len);
|
||||
printf("wrote %d of %zu bytes\n", wrote, len);
|
||||
if (wrote != len) {
|
||||
fail("failed to write all of output at once");
|
||||
}
|
||||
close(fd);
|
||||
printf("Wrote %zu bytes to %s\n", len, path);
|
||||
}
|
||||
|
||||
int main(int nargs, char **argv) {
|
||||
char *spath = argv[1];
|
||||
int fd = open(spath, O_RDONLY, 0);
|
||||
size_t len;
|
||||
char *input;
|
||||
char *output;
|
||||
int seed = 0;
|
||||
if (fd < 0) {
|
||||
fail("cannot open input file");
|
||||
}
|
||||
len = filesize(spath);
|
||||
input = malloc(len);
|
||||
output = malloc(BUFSIZE);
|
||||
if (!input || !output) {
|
||||
fail("failed to allocate buffers\n");
|
||||
}
|
||||
radamsa_init();
|
||||
if (len != read(fd, input, len)) {
|
||||
fail("failed to read the entire sample at once");
|
||||
}
|
||||
while(seed++ < 100) {
|
||||
size_t n;
|
||||
n = radamsa((uint8_t *) input, len, (uint8_t *) output, BUFSIZE, seed);
|
||||
write_output(output, n, seed);
|
||||
printf("Fuzzed %zu -> %zu bytes\n", len, n);
|
||||
}
|
||||
printf("library test passed\n");
|
||||
free(output);
|
||||
free(input);
|
||||
return 0;
|
||||
}
|
||||
|
||||
30853
src/third_party/libradamsa/libradamsa.c
vendored
30853
src/third_party/libradamsa/libradamsa.c
vendored
File diff suppressed because it is too large
Load Diff
13
src/third_party/libradamsa/radamsa.h
vendored
13
src/third_party/libradamsa/radamsa.h
vendored
@ -1,13 +0,0 @@
|
||||
#include <inttypes.h>
|
||||
#include <stddef.h>
|
||||
|
||||
void radamsa_init(void);
|
||||
|
||||
size_t radamsa(uint8_t *ptr, size_t len,
|
||||
uint8_t *target, size_t max,
|
||||
unsigned int seed);
|
||||
|
||||
size_t radamsa_inplace(uint8_t *ptr,
|
||||
size_t len,
|
||||
size_t max,
|
||||
unsigned int seed);
|
||||
107
test/test.sh
107
test/test.sh
@ -23,7 +23,7 @@ else
|
||||
fi
|
||||
|
||||
test_compcov_binary_functionality() {
|
||||
RUN="../afl-showmap -o /dev/null -- $1"
|
||||
RUN="../afl-showmap -m ${MEM_LIMIT} -o /dev/null -- $1"
|
||||
$RUN 'LIBTOKENCAP' | grep 'your string was LIBTOKENCAP' \
|
||||
&& $RUN 'BUGMENOT' | grep 'your string was BUGMENOT' \
|
||||
&& $RUN 'BANANA' | grep 'your string started with BAN' \
|
||||
@ -459,24 +459,23 @@ test -e ../afl-clang-lto -a -e ../afl-llvm-lto-instrumentation.so && {
|
||||
}
|
||||
rm -f test-instr.plain
|
||||
|
||||
# Disabled whitelist until I have a different solution -mh
|
||||
# echo foobar.c > whitelist.txt
|
||||
# AFL_LLVM_WHITELIST=whitelist.txt ../afl-clang-lto -o test-compcov test-compcov.c > test.out 2>&1
|
||||
# test -e test-compcov && {
|
||||
# grep -q "No instrumentation targets found" test.out && {
|
||||
# $ECHO "$GREEN[+] llvm_mode LTO whitelist feature works correctly"
|
||||
# } || {
|
||||
# $ECHO "$RED[!] llvm_mode LTO whitelist feature failed"
|
||||
# CODE=1
|
||||
# }
|
||||
# } || {
|
||||
# $ECHO "$RED[!] llvm_mode LTO whitelist feature compilation failed"
|
||||
# CODE=1
|
||||
# }
|
||||
# rm -f test-compcov test.out whitelist.txt
|
||||
echo foobar.c > whitelist.txt
|
||||
AFL_DEBUG=1 AFL_LLVM_WHITELIST=whitelist.txt ../afl-clang-lto -o test-compcov test-compcov.c > test.out 2>&1
|
||||
test -e test-compcov && {
|
||||
grep -q "No instrumentation targets found" test.out && {
|
||||
$ECHO "$GREEN[+] llvm_mode LTO whitelist feature works correctly"
|
||||
} || {
|
||||
$ECHO "$RED[!] llvm_mode LTO whitelist feature failed"
|
||||
CODE=1
|
||||
}
|
||||
} || {
|
||||
$ECHO "$RED[!] llvm_mode LTO whitelist feature compilation failed"
|
||||
CODE=1
|
||||
}
|
||||
rm -f test-compcov test.out whitelist.txt
|
||||
../afl-clang-lto -o test-persistent ../examples/persistent_demo/persistent_demo.c > /dev/null 2>&1
|
||||
test -e test-persistent && {
|
||||
echo foo | ../afl-showmap -o /dev/null -q -r ./test-persistent && {
|
||||
echo foo | ../afl-showmap -m none -o /dev/null -q -r ./test-persistent && {
|
||||
$ECHO "$GREEN[+] llvm_mode LTO persistent mode feature works correctly"
|
||||
} || {
|
||||
$ECHO "$RED[!] llvm_mode LTO persistent mode feature failed to work"
|
||||
@ -638,43 +637,43 @@ test -e ../libdislocator.so && {
|
||||
INCOMPLETE=1
|
||||
}
|
||||
rm -f test-compcov
|
||||
test -e ../libradamsa.so && {
|
||||
# on FreeBSD need to set AFL_CC
|
||||
test `uname -s` = 'FreeBSD' && {
|
||||
if type clang >/dev/null; then
|
||||
export AFL_CC=`command -v clang`
|
||||
else
|
||||
export AFL_CC=`$LLVM_CONFIG --bindir`/clang
|
||||
fi
|
||||
}
|
||||
test -e test-instr.plain || ../afl-clang-fast -o test-instr.plain ../test-instr.c > /dev/null 2>&1
|
||||
test -e test-instr.plain || ../afl-gcc-fast -o test-instr.plain ../test-instr.c > /dev/null 2>&1
|
||||
test -e test-instr.plain || ../${AFL_GCC} -o test-instr.plain ../test-instr.c > /dev/null 2>&1
|
||||
test -e test-instr.plain && {
|
||||
mkdir -p in
|
||||
printf 1 > in/in
|
||||
$ECHO "$GREY[*] running afl-fuzz with radamsa, this will take approx 10 seconds"
|
||||
{
|
||||
../afl-fuzz -RR -V10 -m ${MEM_LIMIT} -i in -o out -- ./test-instr.plain
|
||||
} >>errors 2>&1
|
||||
test -n "$( ls out/queue/id:000001* 2>/dev/null )" && {
|
||||
$ECHO "$GREEN[+] libradamsa performs good - and very slow - mutations"
|
||||
} || {
|
||||
echo CUT------------------------------------------------------------------CUT
|
||||
cat errors
|
||||
echo CUT------------------------------------------------------------------CUT
|
||||
$ECHO "$RED[!] libradamsa failed"
|
||||
CODE=1
|
||||
}
|
||||
rm -rf in out errors test-instr.plain
|
||||
} || {
|
||||
$ECHO "$YELLOW[-] compilation of test target failed, cannot test libradamsa"
|
||||
INCOMPLETE=1
|
||||
}
|
||||
} || {
|
||||
$ECHO "$YELLOW[-] libradamsa is not compiled, cannot test"
|
||||
INCOMPLETE=1
|
||||
}
|
||||
#test -e ../libradamsa.so && {
|
||||
# # on FreeBSD need to set AFL_CC
|
||||
# test `uname -s` = 'FreeBSD' && {
|
||||
# if type clang >/dev/null; then
|
||||
# export AFL_CC=`command -v clang`
|
||||
# else
|
||||
# export AFL_CC=`$LLVM_CONFIG --bindir`/clang
|
||||
# fi
|
||||
# }
|
||||
# test -e test-instr.plain || ../afl-clang-fast -o test-instr.plain ../test-instr.c > /dev/null 2>&1
|
||||
# test -e test-instr.plain || ../afl-gcc-fast -o test-instr.plain ../test-instr.c > /dev/null 2>&1
|
||||
# test -e test-instr.plain || ../${AFL_GCC} -o test-instr.plain ../test-instr.c > /dev/null 2>&1
|
||||
# test -e test-instr.plain && {
|
||||
# mkdir -p in
|
||||
# printf 1 > in/in
|
||||
# $ECHO "$GREY[*] running afl-fuzz with radamsa, this will take approx 10 seconds"
|
||||
# {
|
||||
# ../afl-fuzz -RR -V10 -m ${MEM_LIMIT} -i in -o out -- ./test-instr.plain
|
||||
# } >>errors 2>&1
|
||||
# test -n "$( ls out/queue/id:000001* 2>/dev/null )" && {
|
||||
# $ECHO "$GREEN[+] libradamsa performs good - and very slow - mutations"
|
||||
# } || {
|
||||
# echo CUT------------------------------------------------------------------CUT
|
||||
# cat errors
|
||||
# echo CUT------------------------------------------------------------------CUT
|
||||
# $ECHO "$RED[!] libradamsa failed"
|
||||
# CODE=1
|
||||
# }
|
||||
# rm -rf in out errors test-instr.plain
|
||||
# } || {
|
||||
# $ECHO "$YELLOW[-] compilation of test target failed, cannot test libradamsa"
|
||||
# INCOMPLETE=1
|
||||
# }
|
||||
#} || {
|
||||
# $ECHO "$YELLOW[-] libradamsa is not compiled, cannot test"
|
||||
# INCOMPLETE=1
|
||||
#}
|
||||
|
||||
test -z "$AFL_CC" && {
|
||||
if type gcc >/dev/null; then
|
||||
|
||||
@ -1 +1 @@
|
||||
04765d30
|
||||
0ca7a8f2
|
||||
|
||||
Submodule unicorn_mode/unicornafl updated: 04765d30ac...0ca7a8f22b
Reference in New Issue
Block a user