* Initial host server skeleton. * Create IASProxy project, and skeleton for attestation host. * Fix up tests * Extend attestation host skeleton, and make test ports configurable. * Enhance MockIAS to make pseManifestStatus optional. * Make IASProxy endpoints asynchronous. * Add sub-modules for challenger and for common code. * Create integration test for host's provisioning endpoint. * Flesh out attestation challenger WAR. * Package refactoring, to be more Java9 friendly. * Refactor more messages into attestation-common. * Remove our private key from the repository. * Declare an empty PSE Manifest to be invalid. * Fix basic integration test issues for challenger and host. * Integrate keystore scripts into the build properly. * Name keystore targets explicitly for Gradle. * Allow HTTP conversation between Challenger, Host and ISV using session ID. * Add MockHost for challenger's integration tests. * Reconcile HTTP port numbers between Phase1 and Phase2 components. * Remove elements that can be inherited from root project. * Add placeholder README. * Add convenient extension functions to ObjectMapper. * Extend integration test coverage for challenger/host/isv. * Catch IOException from HttpClient for challenger. * Integrate host sub-module with remote-attestation project. * Begin integrating host/enclave code from Phase I. * Rename challenger's HTTP endpoint. * Generate keystore for challenger "on the fly". * Add native JNI code for accessing the SGX enclave. * Point Gradle to the correct enclave object. * Fixes for generating a Quote for this enclave. * Return the IAS report to the challenger for verification. * Begin populating the challenger's AttestationResponse message. * Enable the challenger to pass encrypted secrets into the enclave. * Align challenger, host and isv ports. * Refactor challenger as a fat-jar application. * AttestationResponse is not shared, so refactor into challenger. * Move HttpClientContext objects into HttpClient blocks. * Remove unused Message2 and Message3 objects. * Add realistic dummy value for reportID from IAS. * Small tidy-up on attestation host. * First set of review comments. * Add missing exception message. * Update location of environment file. * Use empty mock revocation lists by default. * Improve logging and add "happy path" test for provisioning secrets. * Update Gradle files so that we can run attestation-host from IntelliJ. * The platformInfo field from IAS can be null, so allow this. Also protect other JNI pointer parameters from NPE. * Allow Gradle to build hardware enclave. |
||
|---|---|---|
| .. | ||
| attestation-challenger | ||
| attestation-common | ||
| attestation-host | ||
| attestation-server | ||
| enclave | ||
| gradle/wrapper | ||
| host | ||
| ias-proxy | ||
| build.gradle | ||
| challenger-flow.png | ||
| gradlew | ||
| gradlew.bat | ||
| README-Phase2.md | ||
| README.md | ||
| settings.gradle | ||
Remote Attestation
Project Organisation
-
Enclave
The enclave (
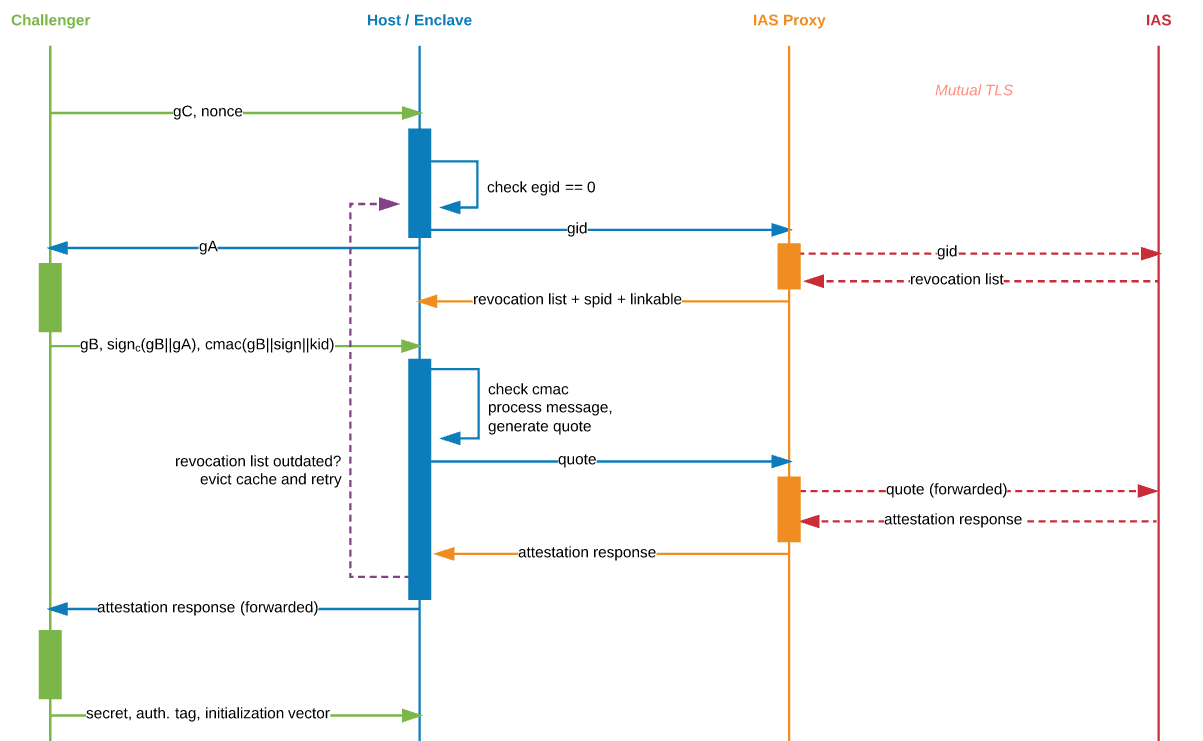
enclave/) is responsible for initialising and coordinating the remote attestation process from the client side, and will eventually operate on a secret provisioned from the challenger (once successfully attested by Intel's Attestation Service). -
Host
The host JVM (
host/) is running in an untrusted environment and facilitates the communication between the challenger and its enclave. To coordinate with the enclave, the host uses a native JNI library (inhost/native/) -
Challenger
The challenger JVM does not require SGX-enabled hardware and is essentially the party asking the host to prove that it has spun up a program in an enclave on trusted hardware (that cannot be tampered with), so that consequently, it can provision an encrypted secret to said enclave.
-
IAS Proxy
The proxy is responsible for talking to the Intel Attestation Service over mutual TLS to verify attestation evidence received from the host. The proxy needs a client certificate and a service provider identifier (SPID) issued by Intel. In turn, it will forward any received proof from Intel to the host and challenger, making it possible for the challenger to trust the host and thus provision the secret. The proof is signed with Intel's root certificate.
Getting Started
To get started, run the following commands in sgx-jvm:
> source environment
> sx help
Further documentation is available in sgx-jvm/tools/sx/README.md.